Kubernetes Security Through Styra DAS: Pre-built PCI Policy Packs
Not only has cloud native transformed the velocity in which organizations execute and maintain business operations, but it has also redefined storage, network and compute. From the infrastructure that IT operations maintains, to the applications that supply customers with the ability to interact with their data—DevOps teams have to deliver more services than ever, and they have to do it fast, with little to no error. Easy, right? 😉 Just to make it more challenging, DevOps teams must also adhere to regulatory compliance standards and frameworks, oftentimes having to manually write the policies and prove application of those policies in an effort to pass an audit.
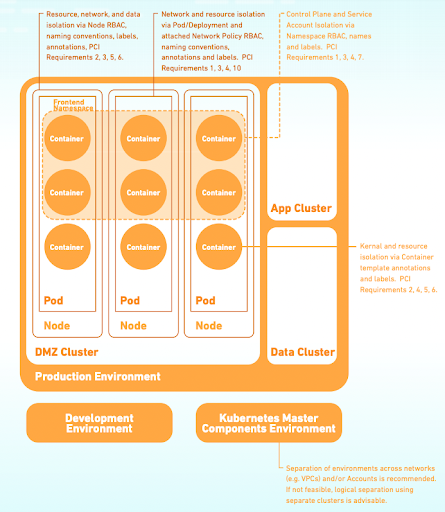
One of the main use cases Styra Declarative Authorization Service (DAS) supports is Payment Card Industry Data Security Standard (PCI DSS) v3.2. While v3.2 doesn’t have a true cloud-native approach, v4.0 later this year might. However, in v3.2 a lot of the requirements can be leveraged throughout a cloud environment where cardholder and sensitive data is processed, transmitted or stored. The 12 high-level requirements are broken down into functional testing procedures which can help organizations implement the proper policies for handling sensitive data.
Styra maps to requirements 1, 2, 3, 4, 5, 6, 7, and 10 – with 40 sub-requirements and is supported by pre-built policies to help organizations establish and maintain compliance. It is important to note that the requirements that we do not map to are still critical to organizations and can be found in other solutions that span different areas of focus.
Styra enables organizations to maintain their desired velocity by ensuring that teams can quickly and efficiently validate compliance, maintain clear logs for audit, test policies before production to reduce down-time and provide a unified control plane for cross-team collaboration.
Pre-Mapped PCI DSS v3.2 controls to Kubernetes policies
Can you imagine a world where you don’t have to try to read through 130+ pages of compliance standards, distill that information into real measures your organization can take, and then also do the mapping exercise so you can prove compliance when the auditor comes knocking? Styra has set out to make this process easier for organizations that already have enough on their plate so you can dynamically run your policies through a mapped library of PCI requirements.
Time reduction on audit reporting
Oh no. The dreaded auditor. I mean don’t get me wrong, it is a valuable task to complete for any organization and does help to have a non-biased set of eyes on your infrastructure, but oh goodness it really does just throw a wrench in an organization’s day-to-day operations. As many folks can attest, allocating resources to assist the auditor in the collection, understanding and assessment of the policies that impact credit card data just sucks. We created a way that drastically reduces the amount of resources needed to assist the auditor via automated compliance reporting for running clusters and a supplemental ongoing audit log of compliance decisions to prove compliance, without having to step through policy-as-code line-by-line. Too good to be true, right?!?! It is true .
Ensuring comprehensive controls
With the addition of compliance to most development lifecycles, that means an increase in the number of team members that are contributing to an application or applications. Organizations can’t have a disruption or lost time while trying to organize all of the moving pieces. They need to maintain continuity of the desired outcome and establish true comprehensive controls for success. We saw this as a great way to help organizations so we designed out-of-the-box, easy to configure, policies that some of the largest Kubernetes deployments on the planet use today.
Cross-team collaboration with DevOps, SOC, I&O (IT), and GRC
While Kubernetes can seem like one of the greatest tools since the machine that slices bread, it has also introduced the need for multiple teams to be a part of the build process. And with that comes non-coders and coders that need to be able to digest policies and their outcomes. Well…welcome to the playing field, non-coders! We have made a way for you to collaborate and communicate with your awesome coders colleagues about the state of security and compliance in Kubernetes.
Read more on how Styra maps to each PCI DSS v3.2 requirement for Kubernetes, and the best way to address them through pre-built policies.