Announcing our Declarative Authorization Service for K8s
From policy authoring through continuous monitoring and auditing, Styra helps secure your Kubernetes environments through compliance guardrails
A growing number of businesses are adopting Kubernetes today—in fact it has become the de-facto standard for deploying containerized applications at scale in private, public and hybrid cloud. Kubernetes lets businesses speed the process of bringing applications into production, and also increases the agility and efficiency of the software development teams.
In today’s containerized environments, changes are constant, and runtime is extremely dynamic. That’s why it’s more critical than ever to define and implement security guardrails and policies. Kubernetes provides the orchestration to ensure that runtime is always being brought back to desired-state—but that desired state must be well-defined, with clear security guardrails to prevent drift, risk, and accidental missteps.
Today, I’m pleased to announce Styra’s Declarative Authorization Service for Kubernetes. Strya created the open source project Open Policy Agent (OPA), and one of the use cases for OPA has been as a Kubernetes Admission Controller. Many early adopters have used OPA as an Admission Controller and with this in-depth experience and closely working with these early adopters, we have released our first commercial product leveraging OPA. Styra allows teams to define, enforce, and validate security policy. As businesses adopt a hybrid-cloud strategy, it becomes crucial to be able to establish policies that apply to all Kubernetes environments running across hybrid clouds to strengthen policy compliance.
Here’s an overview of the key capabilities:
- Simplifying policy authoring
- Policy validation prior to enforcement
- Policy distribution and enforcement
- Continuous monitoring
- Policy visualization
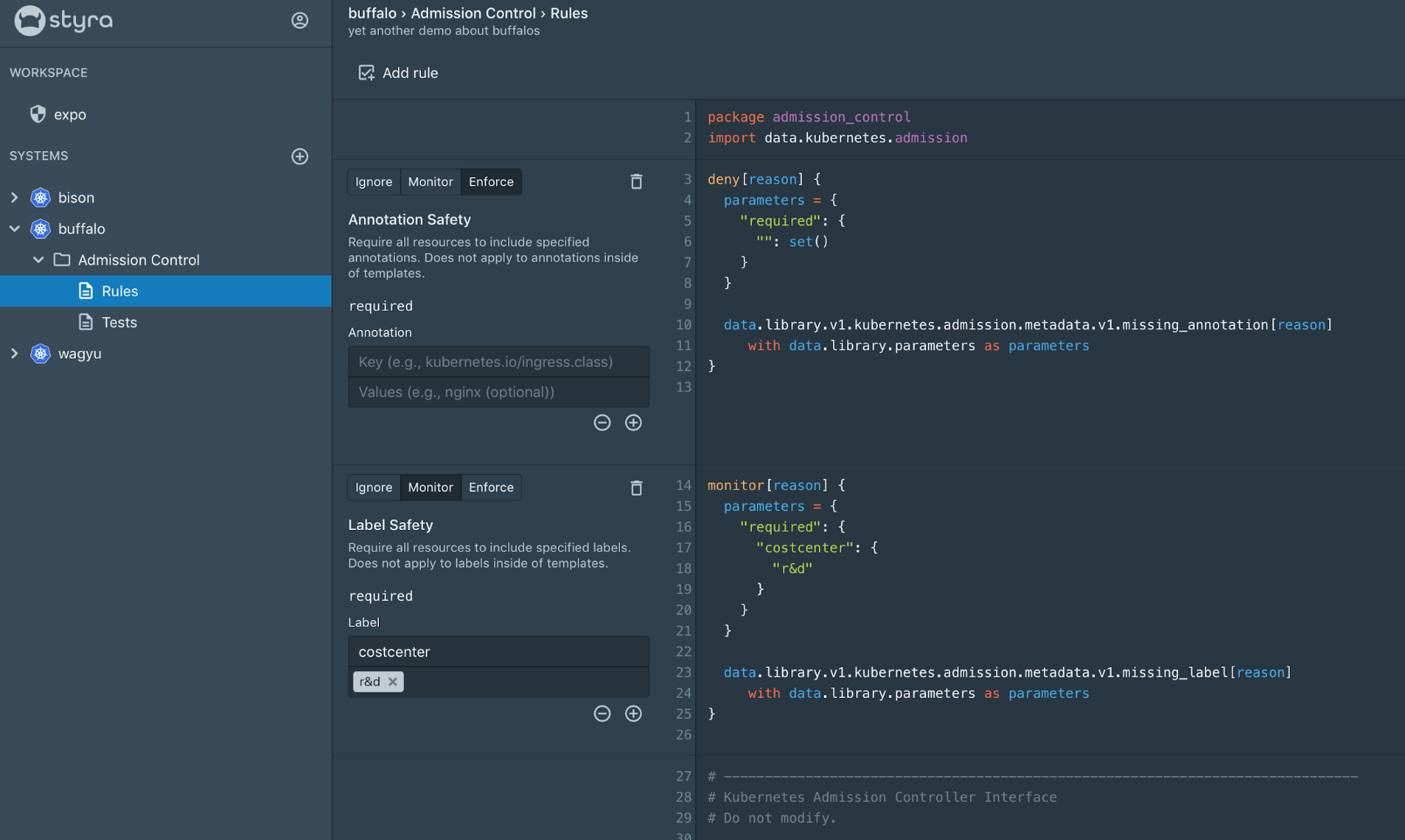
Built-in Policy Library
Styra’s DAS simplifies Kubernetes policy creation with a built-in library of best practices and security policies, all sourced from real-world use cases. This library includes the policies below, and many more:
Repository Safety – Only allow container images pulled from approved registries and (optionally) matching a list of approved repository image paths.
Block Container Privilege Mode – Prevent containers from running in privilege mode
Annotation Safety/Label Safety – Require all resources to include specified annotations or labels
Rich and Varied Policy Authoring Experience
The future of security is policy-as-code. But not every security team is made up of coders. That’s why Styra provides both a point-and-click user interface as well as a rich code editor.
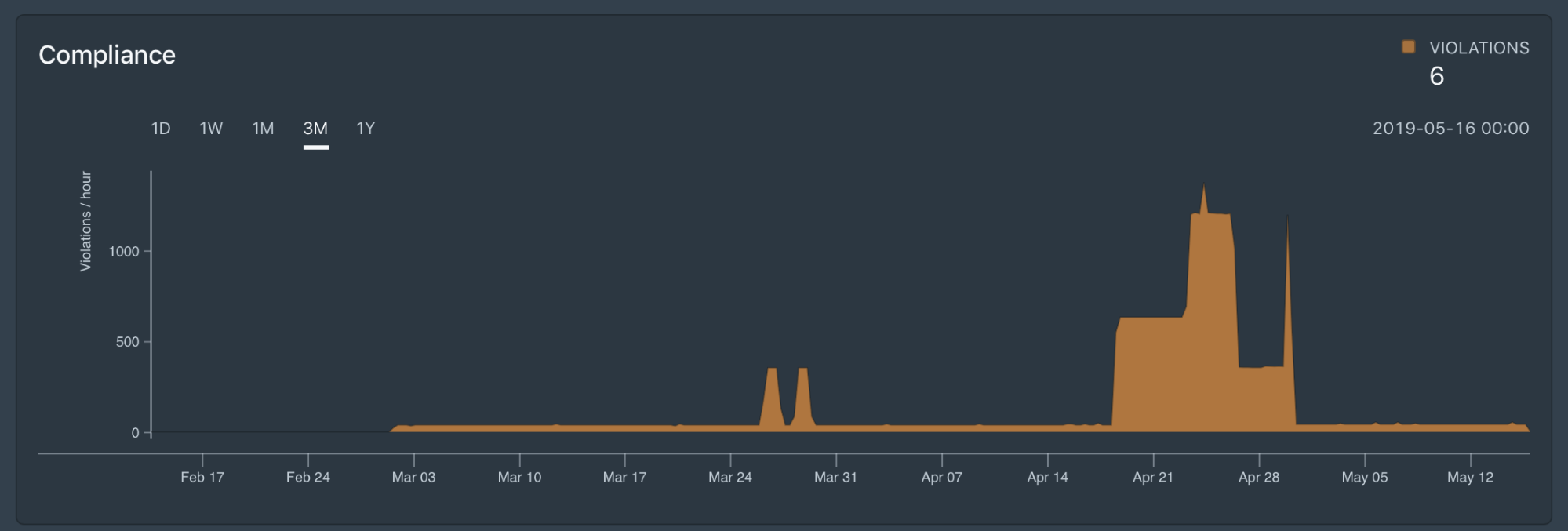
Policy Validation Prior to Enforcement
Styra allows you to pre-run policies to see their impact before deployment for all policies to be able to deploy more confidently. Rules can be put into monitor-only mode to see where violations occur.
This includes three components:
- 1. Unit testing to ensure that policy-as-code will run as intended and provide expected output,
- 2. Policy compliance to validate what changes will be made to the currently running resources if the new policy is deployed, and
- 3. Historical decision replay which compares the new policy against all historical decision data to show the extent of the changes, and validate that the new policy will have the intended effect.
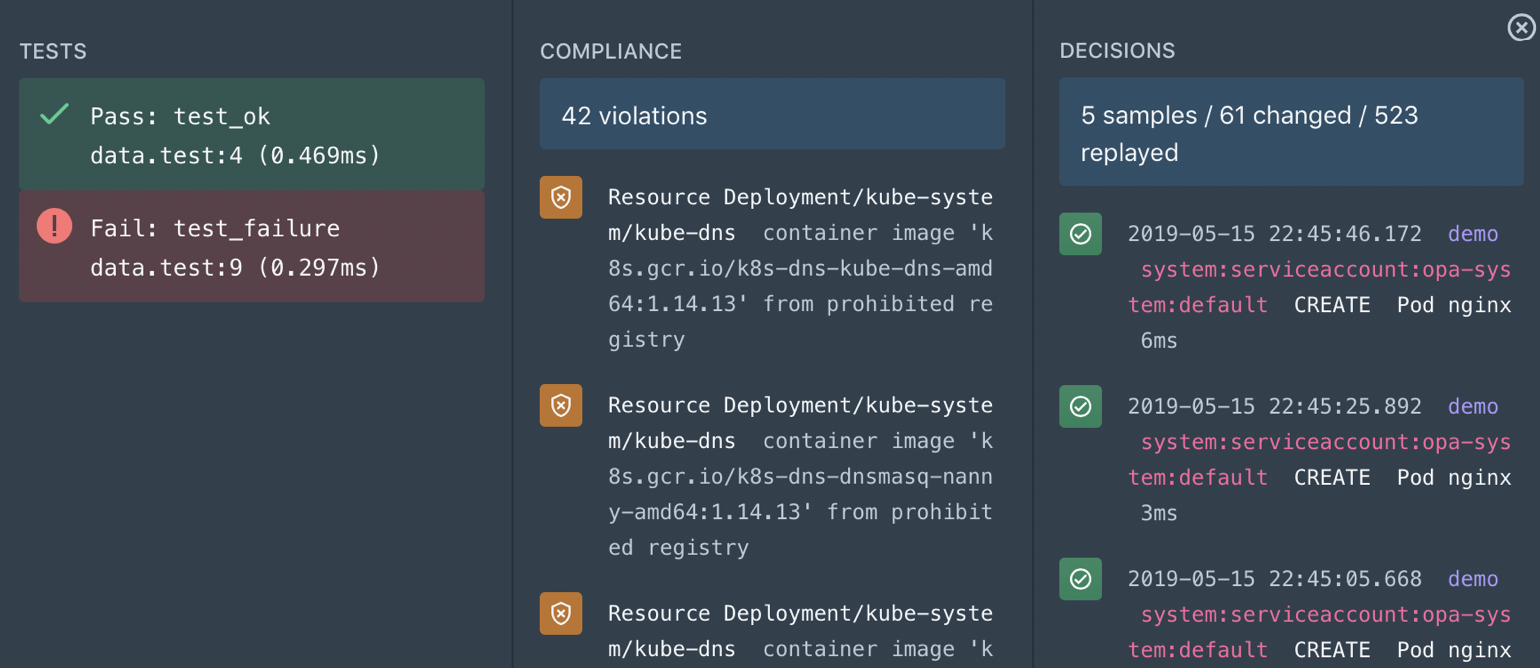
Policy Distribution & Enforcement
Styra uses Open Policy Agent as the policy decision point. OPA is a popular and widely deployed open source project founded by the same team that built Styra. OPA is automatically configured during installation to download bundles of policy and data from Styra. Once the policy is authored and published, the OPA running on each Kubernetes cluster will pull it down the next time it connects to Styra. The delta set of policies and data are loaded on the fly without requiring a restart of OPA. Once the policies and data have been loaded, they are enforced immediately.
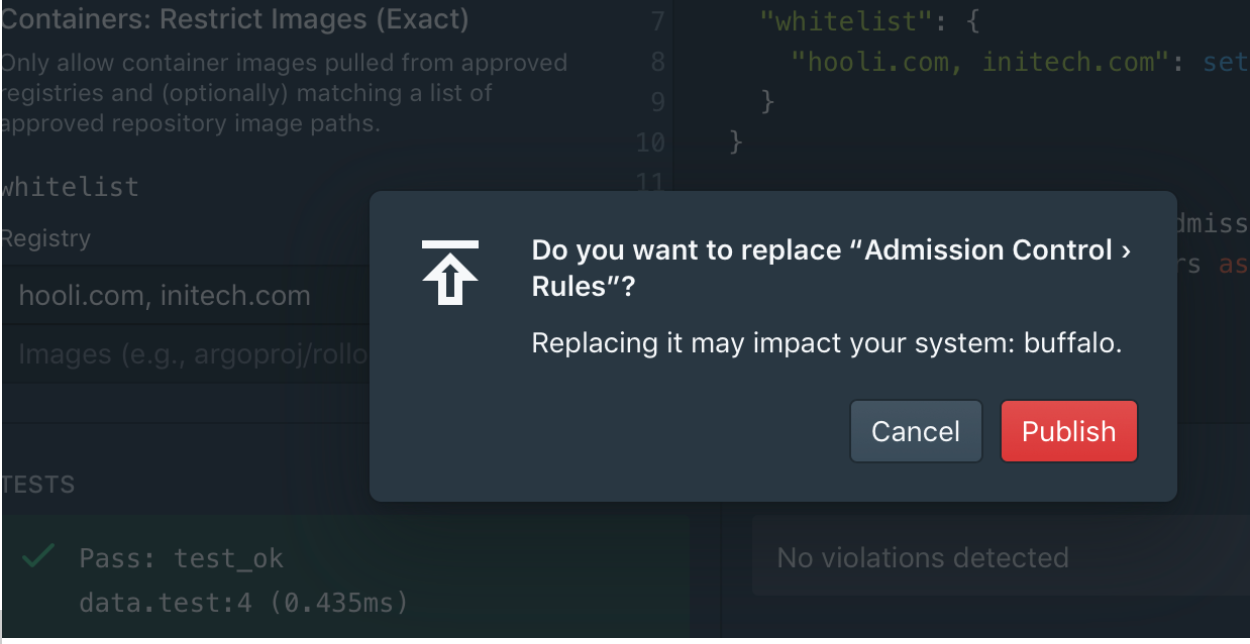
Continuous Monitoring
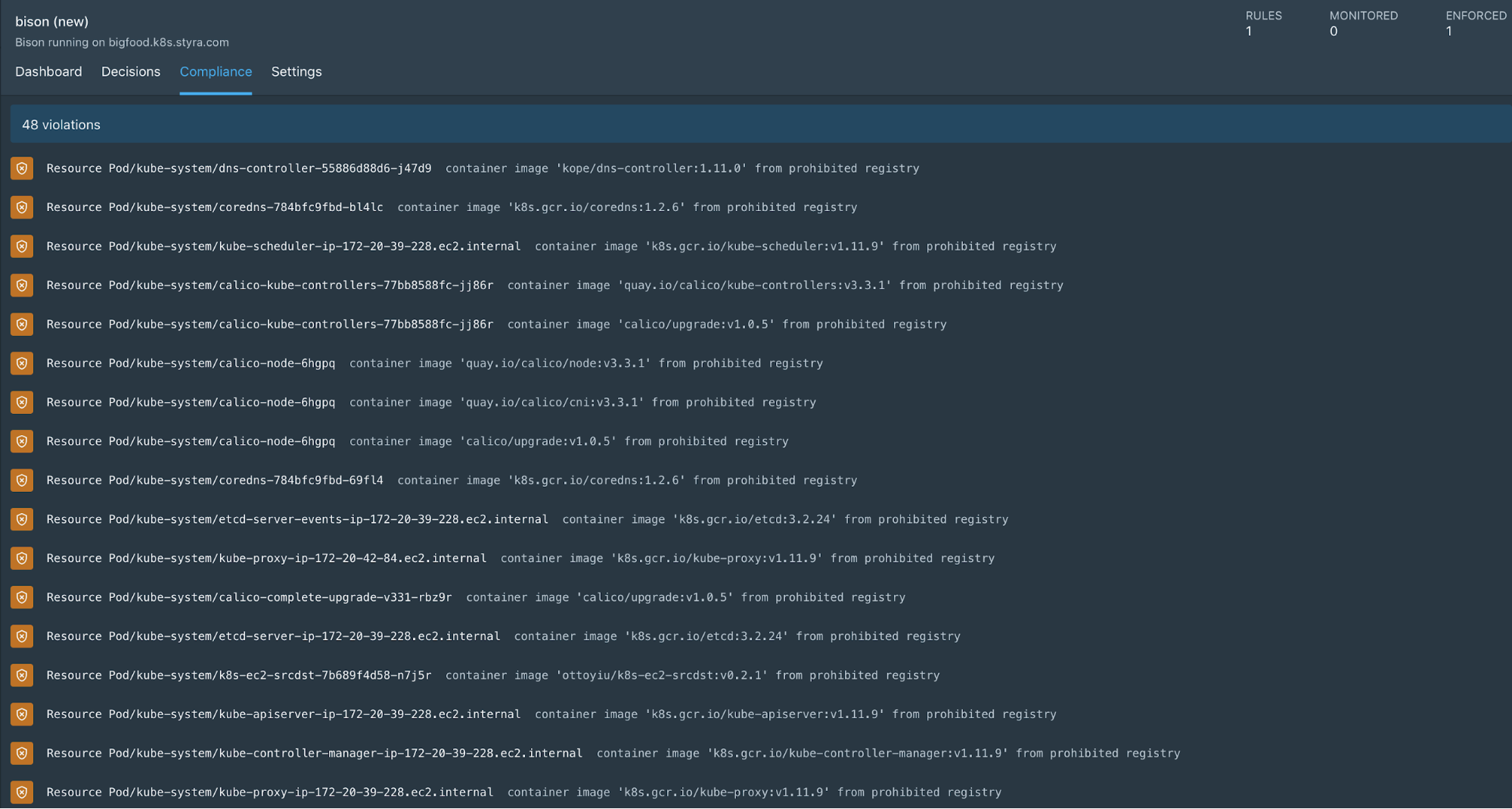
Once policies are in place, Styra continuously monitors policy, meaning that it searches through all the resources on the clusters and finds a list of those that violate the current policy. All the violations are available for remediation in the control plane.
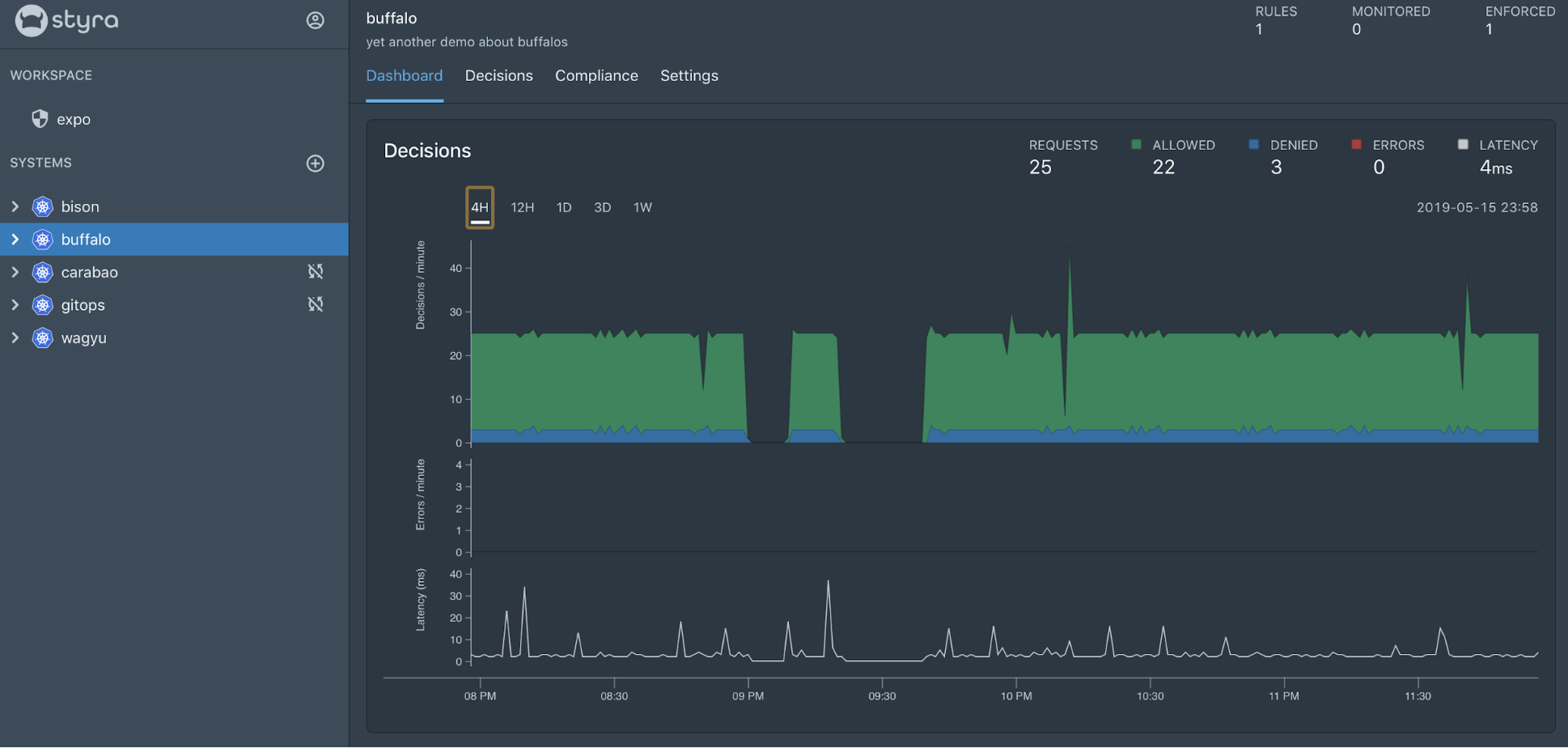
Policy Visualization
Dashboards Styra dashboards provide high-level view of the decisions that are getting made, the denials that OPA is enforcing, and the overall audit violations that are in place. Dashboards are available for Security and DevOps teams to ensure that clusters are operating in compliance with both internal and external regulations.

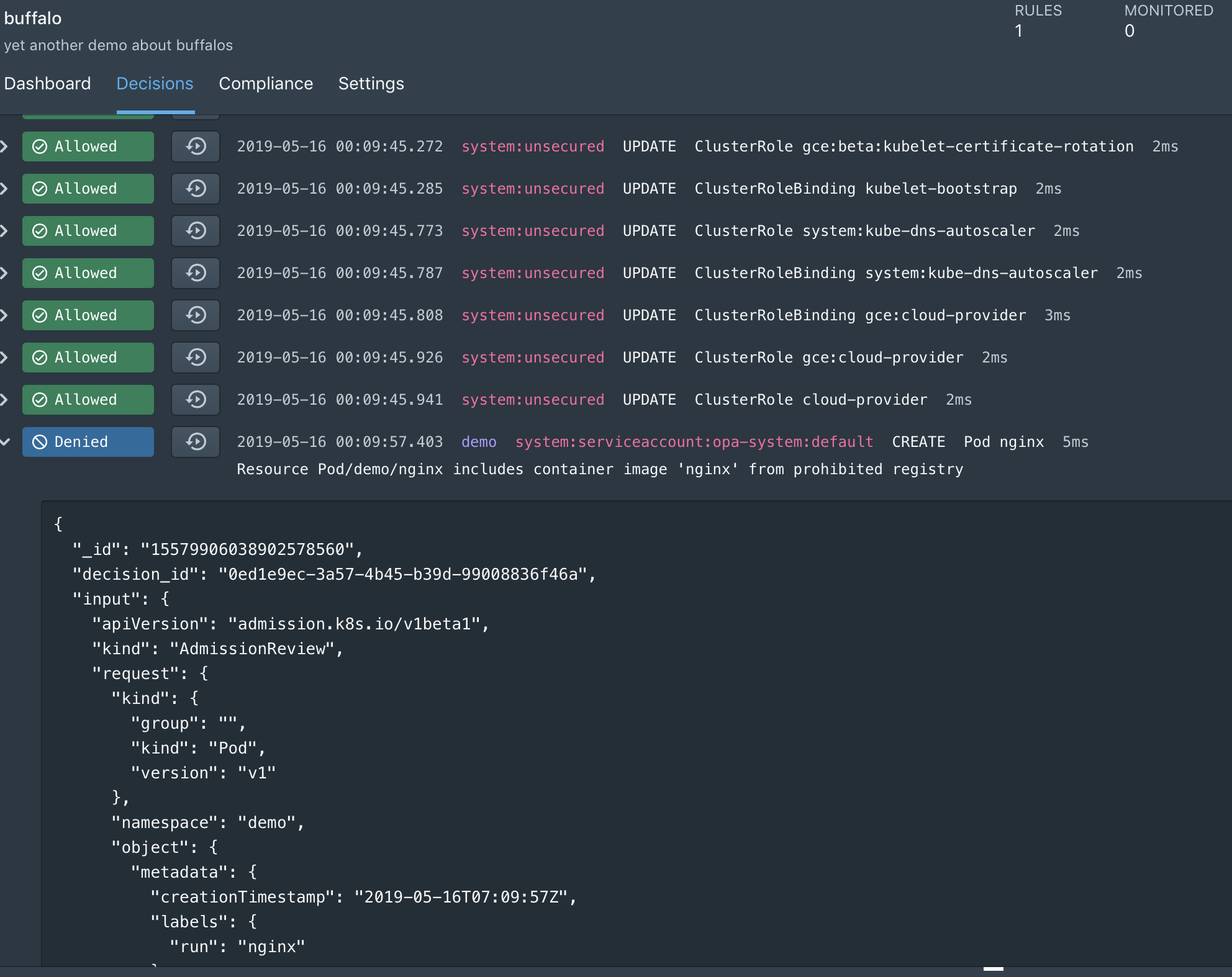
Raw Decision Logs
The Styra control plane shows raw decisions being enforced by OPA in real time. These decisions contain events that describe policy queries. Each event includes the policy that was queried, the input to the query, bundle metadata, and other information that enables auditing and debugging for policy decisions.
Many more policies are being added into the Built-in Policy Library, and the next set of features around addressing SHIFT security left is coming up. Stay tuned!
Ready to try it out?
Styra’s Declarative Authorization Service for Kubernetes is available for our customers now, reach out to us by signing up here!