Open Policy Agent
The #1 general-purpose policy engine, created and maintained by Styra
What is Open Policy Agent?
Open Policy Agent (OPA) provides a purpose-built policy language, policy engine, tooling, and over 100 integrations to help you write and enforce policies across the cloud-native ecosystem.
OPA has the architectural flexibility to meet your performance and availability needs and delivers a policy as code framework that lets you (and your entire organization) manage policy as a first-class citizen.
Its power, speed, reliability, and community have made it an industry standard adopted by some of the world’s most notable enterprises.
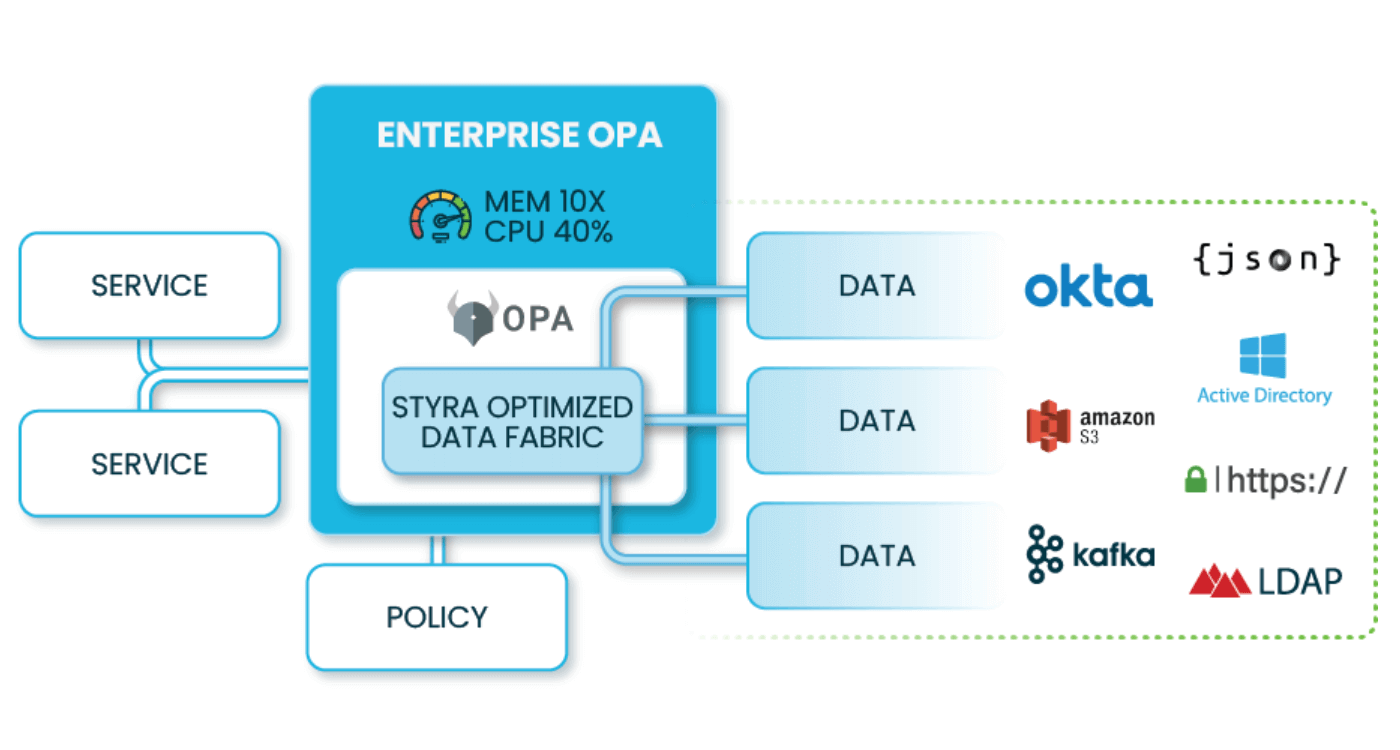
Enterprise OPA
Handles more data, faster.
Enterprise OPA has all the benefits of Open Policy Agent and more:
- Datasource integrations: Connect quickly to your Kafka, Okta, LDAP, S3 to get your access control data without needing to write and manage your custom plugins.
- SQL support: Easily implement ABAC or RBAC with data from MySQL or PostgresQL compatible databases.
- Secrets manager integration: Connect to HashiCorp Vault to securely access external APIs.
- Logging integrations: Send your authorization decision logs to Splunk, Kafka, and S3.
- Live impact analysis: Check to see if your new policies impact production before they are merged.
- Lower infra costs: Enterprise OPA lowers your cloud bill and eco footprint because it uses 10x less memory and 40% less CPU than Open Policy Agent.
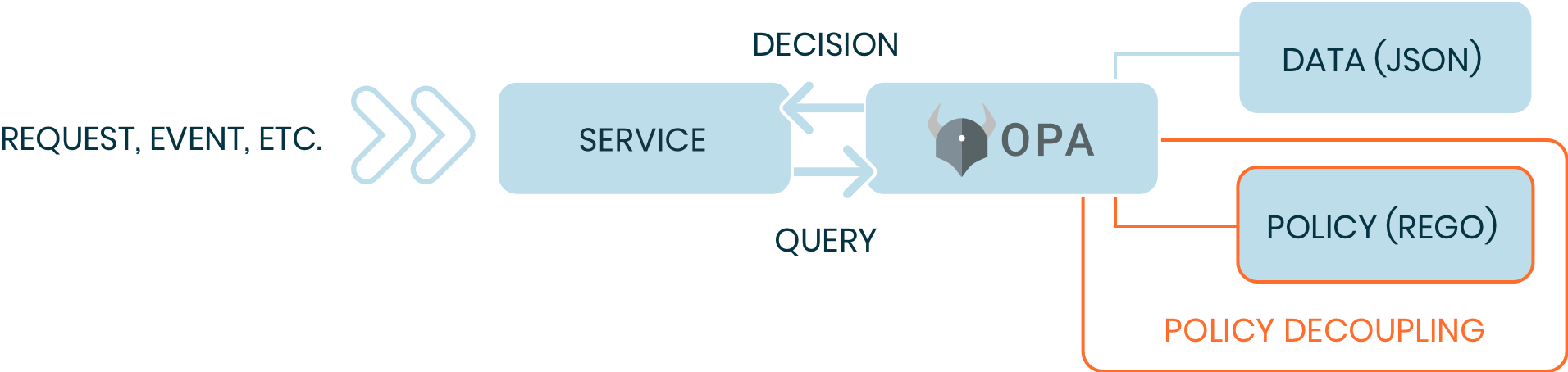
How does OPA work?
OPA is able to handle authorization through its unique policy language, Rego. Using Rego, users can write policy-as-code, define their entire setup, then apply these rules to every running OPA. Open Policy Agent handles incoming requests using their own internalized decision making, expressed through Rego. Using OPA, developers are saved the hassle of downing an entire stack to make changes to a single microservice.
OPA has been integrated by many enterprises and is usable with standard infrastructure tools such as Kubernetes, Envoy, Terraform, and AWS. This makes it a wonderful tool for developers to create their policy-as-code solutions, regardless of how their system looks

CNCF Graduated Open Source Project
For software to become well-adopted, it needs to draw from a wide-ranging pool of knowledge. This is a lot of work for a small team, which led OPA’s founders to donate it as a Sandbox project to the Cloud Native Computing Foundation (CNCF). OPA grew through incubation in the CNCF and achieved Graduated status in 2021.
Why Use Open Policy Agent?
General Purpose
Deploy a single tool for policy enforcement across the cloud-native stack.
Cloud-Native
Built to run in containerized, distributed, cloud-native environments.
Open Source
Users can modify the source code to fit their needs, personal or enterprise.
Rego Language
High-level declarative language makes building policy easy.
Centralized Management
Manage and monitor distributed environments with hundreds of OPAs.
Community Ecosystem
OPA’s open-source status has drawn a passionate community and ecosystem.
Styra Academy
Styra Academy provides an easy to follow Open Policy Agent tutorial for users new to OPA, who need to learn Rego, or simply would like to understand OPA performance better. This free course in our Academy guides users in a step-by-step curriculum so they can get started quickly.
Rego Policy Language
Rego is a high-level coding language that makes it easy for users to build policy around structured hierarchical data (JSON, YAML, etc.) used in most systems. With a unified language and over 150 built-in functions, Rego is one of the key components allowing OPA to unify policy across the stack.
FAQ
What does OPA Do?
OPA is an open source, general purpose policy engine that allows developers to use policy-as-code to enforce authorization across the cloud-native stack. To accomplish this, OPA decouples policy decision making from applications, allowing for uniform policy and increased application performance. Thanks to its declarative language policy language, Rego, OPA can make decisions for Kubernetes, Microservices, functional application authorization, gateways and more. It structures these policies based upon hierarchical structured data, such as JSON or YAML data, with several use cases of integrations.
How do you deploy an OPA?
OPA is set up with a few major components. To start, users must define some hierarchical structured data for OPA to follow, such as JSON or YAML values. Next, they must write their policy in Rego, either from scratch or using pre-built functions, to allow OPA to make decisions after being contacted via API. Finally, OPA must be run via CLI. This can be done as a Go library or a server, as well as through integrations with third party software such as Docker.
How do I use and integrate Open Policy Agent?
The key to understanding OPA is understanding that it is simply policy-as-code, and it should be understood in a similar way. First, you must determine your requirements, such as where and how you will enforce OPA, and then the data dependencies upon which it will be leaning for its decision making. Next, you must handle setting up OPA for your use case. With several configurations available, this can be a daunting task. However, thanks to OPA’s thriving ecosystem, these integrations and their instructions are available at your fingertips.
Can you Install Open Policy Agent on Linux?
Open Policy Agent is available for Linux, with instructions for how to install the Linux OPA binary via CLI in the documentation.
Cloud native
Authorization
Entitlement Explosion Repair
Join Styra and PACLabs on April 11 for a webinar exploring how organizations are using Policy as Code for smarter Access Control.
Speak with an Engineer
Request time with our team to talk about how you can modernize your access management.