From Code to Cloud: Enforcing Kubernetes and Terraform guardrails via Styra DAS
TL;DR
Whether you use the 600+ Styra provided compliance rules or build your own, with Styra DAS, the same rules can now enforce compliance of your Kubernetes and Terraform infrastructure across all of the Code, Deploy, and Run phases.
What you will learn:
- Why do Kubernetes and Terraform infrastructure need guardrails via Policy-as-Code?
- Why do IaC policy guardrails need to be applied from Code to Cloud?
- How Styra Declarative Authorization Service (DAS) can be used to manage and monitor your IaC Code-to-Cloud policy guardrails
Why Kubernetes and Terraform infrastructure needs Policy-as-Code guardrails
Infrastructure-as-Code (IaC) has allowed for infrastructure automation to replace manual provisioning, enabling developers to self-service deploying cloud resources. This raises a new problem: how to make sure self-service provisioned infrastructure remains compliant with security best practices and organization requirements.
Making sure your infrastructure has “policy guardrails” is a necessary step in maturing your platform team’s security practices. The gold standard approach to infrastructure policy guardrails comes from the Open Policy Agent (OPA) idea of “Policy-as-Code,” which has been adopted by Kubernetes (via Admission Control and Gatekeeper) and Terraform (via Terraform Cloud Runs). We firmly believe that Policy-based access management and infrastructure guardrails are the future!
Code, Deploy, Run: Why IaC policy guardrails need to be applied from Code to Cloud
One of the benefits of combining Infrastructure-as-Code and Policy-as-Code is that you can run your policies at all phases of the IaC DevOps cycle: code, deploy, and run –– or what we call “Code-to-Cloud.”
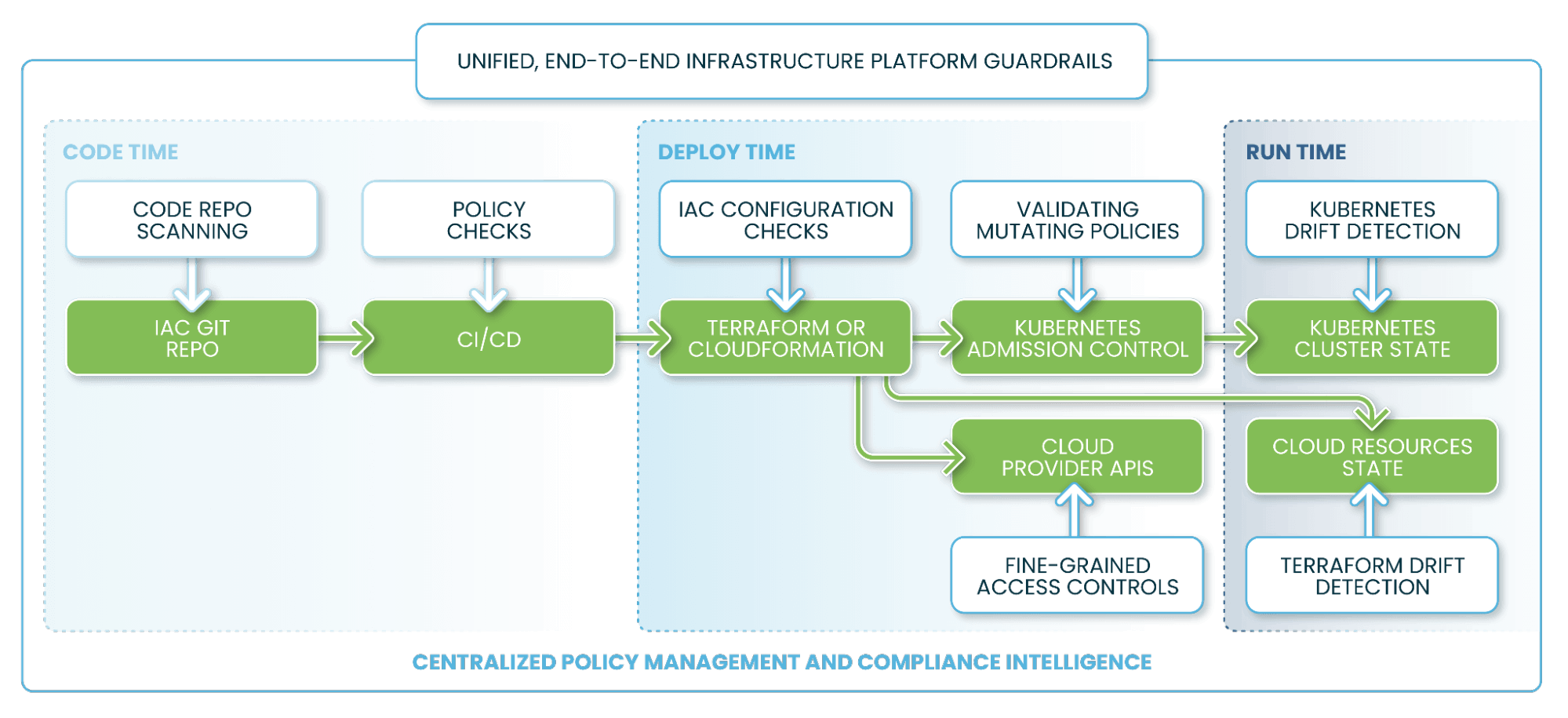
This provides several checkpoints where non-compliant infrastructure can be caught and remediated – including before it gets deployed into production – improving your security posture. This is the essence of putting your infrastructure “on guardrails.”
How Styra DAS can be used to manage and monitor your IaC policy guardrails across code-to-cloud.
Kubernetes and Terraform use several different artifacts to represent their infrastructure across Code, Deploy, and Run phases. Styra DAS supports applying policy guardrails across all of those artifacts:
- Kubernetes: YAML manifest files (Code), AdmissionReview objects (Deploy) and JSON cluster resource states (Run)
- Terraform: .tf and .tf.json HCL files (Code), JSON plans (Deploy), JSON-encoded Terraform state and Terraformer JSON plan files (Run)
These IaC artifacts each have different file types and schemas, which would normally make policy authoring quite complex or require transforming the inputs into a unified format. Our competition’s solution to this problem is to transform the input types into proprietary and non-standard input representations. Styra DAS instead transforms these IaC input types into standardized and open-source JSON input objects: AdmissionReview JSON objects for Kubernetes inputs and JSON plans for Terraform inputs.
Enforce Compliance during Code Phase
To enforce compliance during the Code phase, use the Styra CLI `validate check-local` command against Kubernetes YAML manifest files (.yaml) and Terraform HCL files (.tf and .tf.json)
The command is flexible enough to be used to manually check for compliance by running the command locally, or as an automated compliance check in a pre-commit hook, in a cloud git commit, PR, or merge check (e.g., GitHub, Bitbucket) or in CI/CD pipeline build steps (e.g., CircleCI, Jenkins). Here’s an example of the output:
> styra validate check-local
Check `prod_and_staging` failed
Found errors in the following files:
* s3.tf
* iam.tf
Found monitoring errors in the following files:
* s3.tf
* iam.tf
Error: 1 Check Failed
The full results with detailed policy violations are available via the Styra DAS decision logs. Detailed steps for code scanning configuration using the Styra CLI are available in the Styra DAS docs for Kubernetes and Terraform.
Enforce Compliance during Deploy Phase
Kubernetes
OPA can be deployed to a Kubernetes cluster and configured as an admission webhook managed by Styra DAS. OPA is invoked to check each cluster change against policies defined in Styra DAS; violating changes are prevented from deploying to that cluster.
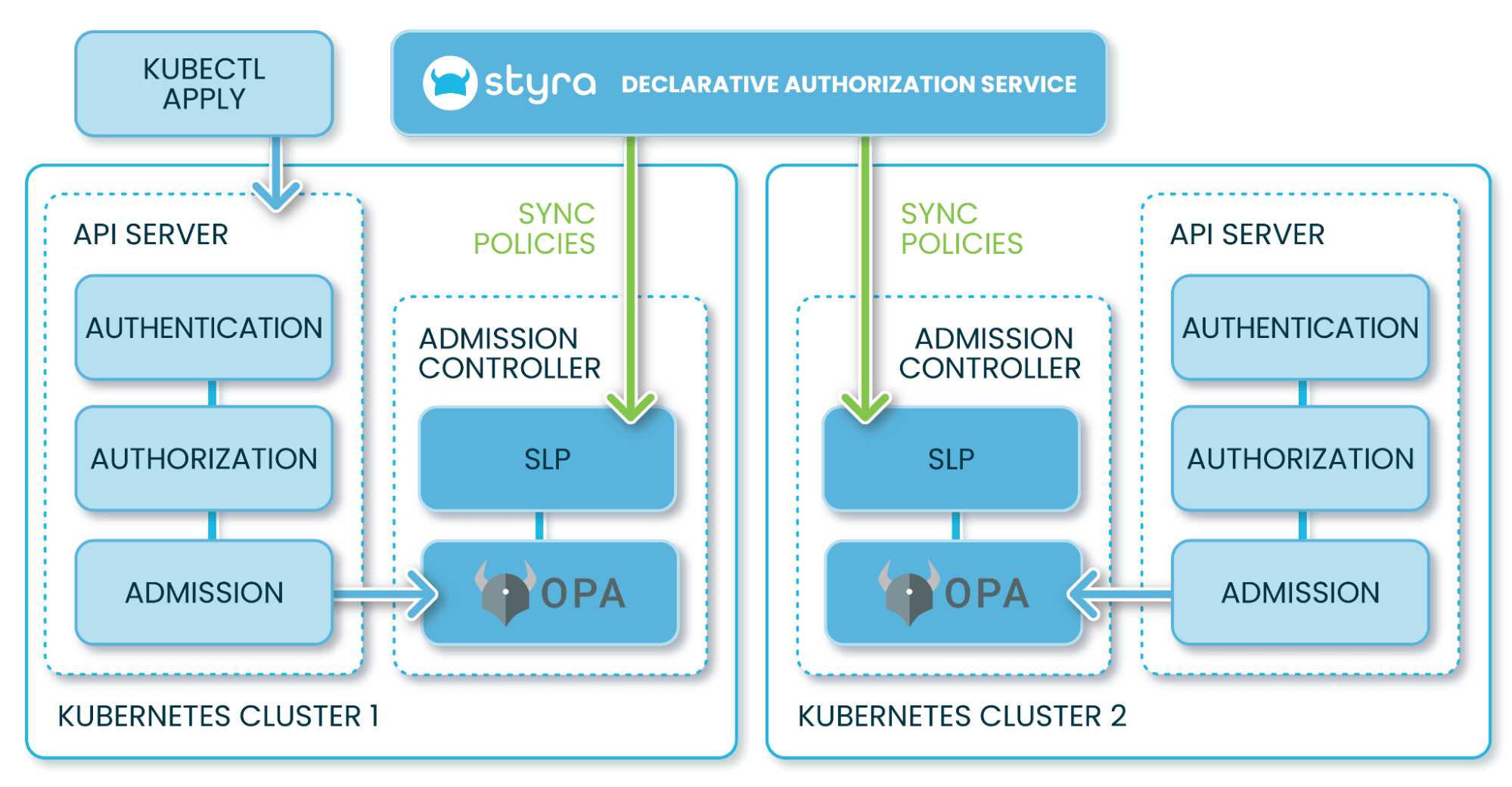
Styra DAS Kubernetes Admission Control Flow
Terraform
Styra DAS can be natively integrated with Terraform Cloud or Terraform Enterprise as a run task. The run task will fail if any resource changes in the Terraform plan are non-compliant.
Alternatively, compliance checks on Terraform plans can be run using the Styra CLI `vet` command (e.g., `styra vet plan.json`). This enables you to enforce compliance in a CI/CD system or in an external Terraform management service, such as env0.
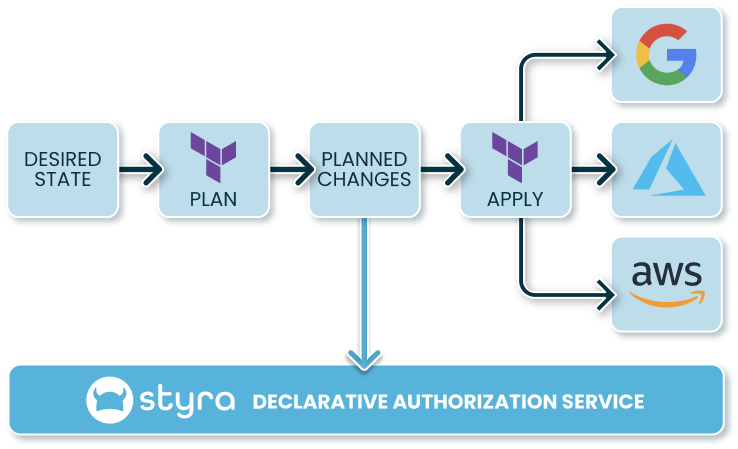
Terraform Plan policy evaluation with Styra DAS
Monitor Compliance during Run Phase
Kubernetes
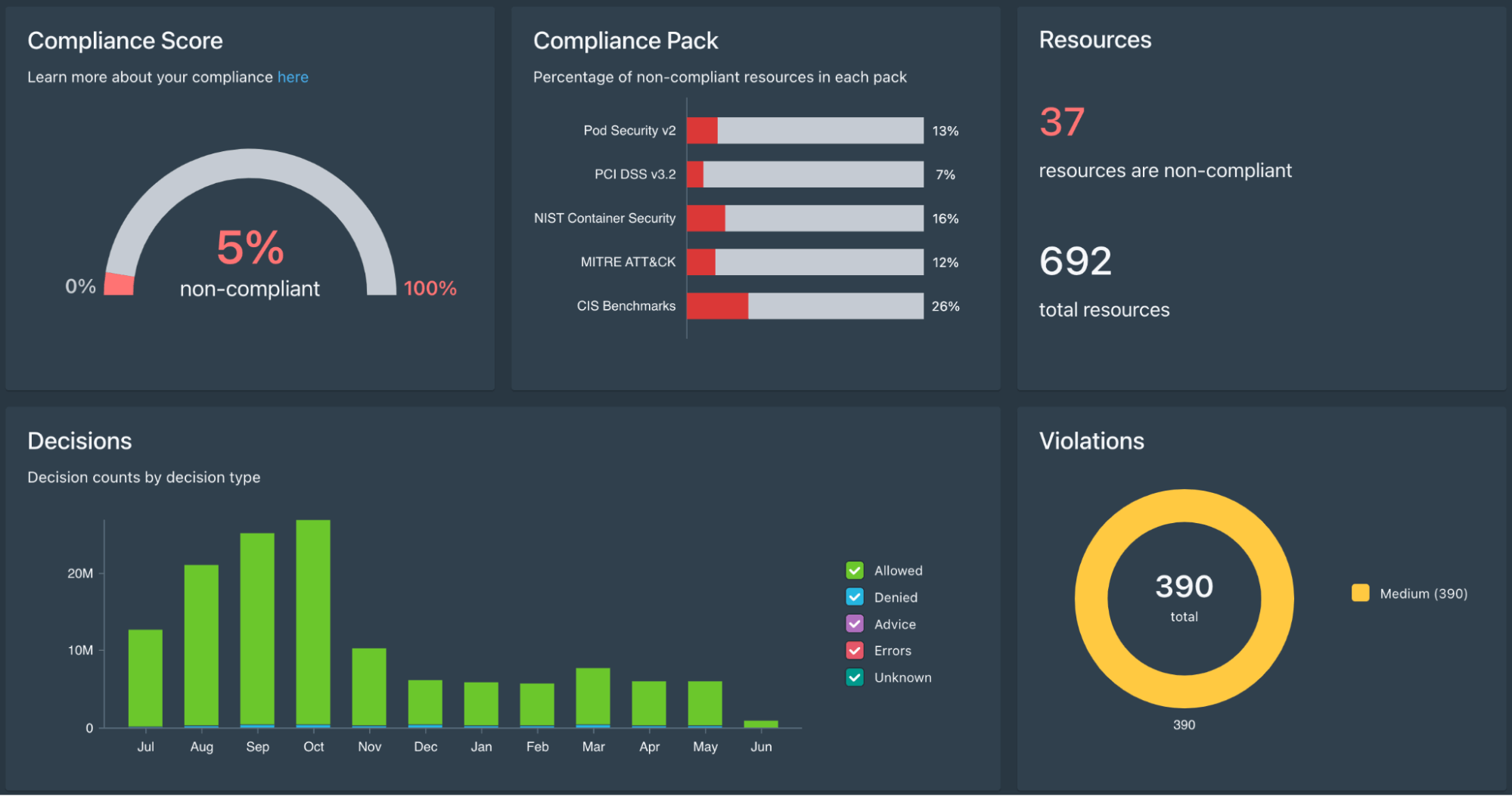
Styra DAS Kubernetes Compliance Dashboard
Styra DAS Compliance monitoring evaluates the same code-to-cloud policies against the current state of the Kubernetes cluster. Violations found during compliance monitoring become immediate targets for review and you can easily report your overall compliance during an audit.
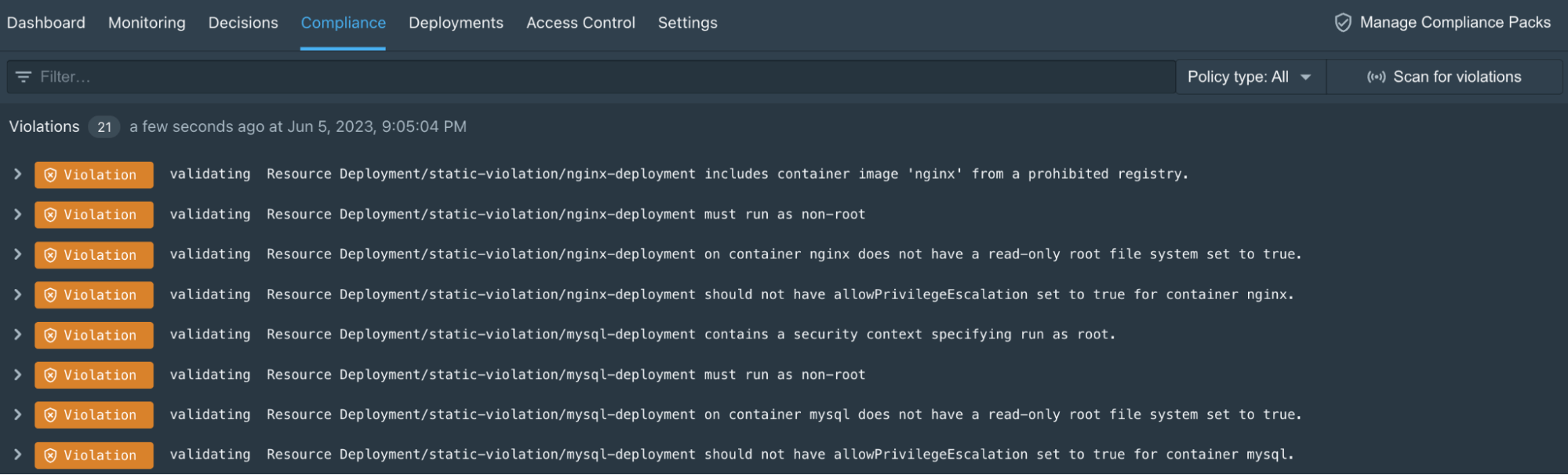
Styra DAS Kubernetes Compliance violations
Terraform
One of the most highly-requested features for Styra DAS Terraform systems, Terraform State Compliance expands the Compliance monitoring functionality customers know and love for Kubernetes to Terraform. Policies are automatically run against Terraform state data to provide visibility into non-compliant resources. This can be used regardless of how you generate and store your Terraform state:
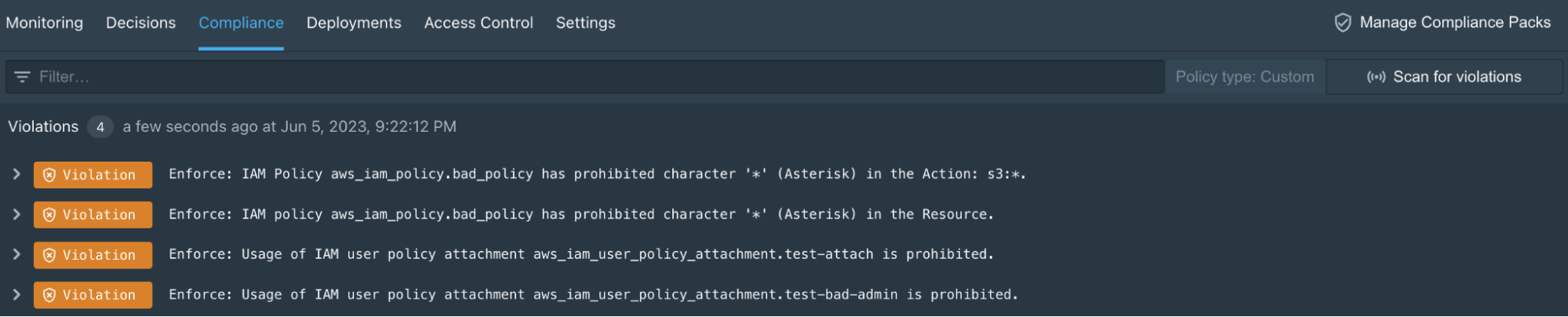
Styra DAS Terraform State Compliance violations
Wrapping Up
Securing Kubernetes and Terraform configurations throughout the DevOps cycle can seem like a daunting task, however the benefits pay dividends in the long-run: frequent developer feedback before code is checked in, reducing manual code review steps, and verification of compliance for deployed resources. With the new Styra DAS features, teams can easily implement the necessary infrastructure policy guardrails for Kubernetes and Terraform for full Code to Cloud coverage.
If you’d like to learn more about using Styra DAS for Terraform, be sure to book some time with a Styra team member today.