The Guide to Kubernetes Compliance
Kubernetes (K8s) has achieved undeniable mainstream status, with 96% of organizations currently evaluating or already using this technology, according to the Cloud Native Computing Foundation (CNCF). This popularity also brings growing scrutiny over Kubernetes compliance standards and audits, in light of how Kubernetes and cloud native technologies demand a very different approach to security.
To ensure proper functioning of your Kubernetes environment and integrity of sensitive data for the sake of protecting your business reputation, compliance across your Kubernetes environments is more critical than ever. This article helps you get started.
Key takeaways:
- Compliance should be a key component of your Kubernetes adoption strategy, helping you secure applications, meet regulatory requirements and keep application development on track.
- Important compliance frameworks include the Center for Internet Security (CIS) Kubernetes Benchmarks and the Payment Card Industry Data Security Standard (PCI DSS), among others.
- Open Policy Agent (OPA) helps dev teams automate Kubernetes compliance. By adding compliance packs from Styra Declarative Authorization Service (DAS), you can ease the operational complexities of meeting regulatory standards.
Make K8s Compliance Management a Strategic Priority
As Gartner notes in its guide to the cloud-native container ecosystem, the fast pace and fragmentation of these environments make them challenging for operational governance. The same dynamism and scalability that contribute to the proliferation of Kubernetes also increase its security and compliance complexity.
In cloud-native architectures, meeting compliance means that the applications adhere to standards, best practices or regulations that ensure security controls and auditing. So, equally important for this process is to maintain accurate records supporting the compliance measures in place.
For 55% of the respondents of Red Hat’s 2022 State of Kubernetes study, K8s compliance is a must-have Kubernetes security capability, while 39% rate it as nice to have.
Depending on the industry, however, meeting certain regulatory requirements is not an option, but rather mandatory. If you are developing a healthcare application that deals with patient Protected Health Information (PHI), for example, you need to comply with the Health Insurance Portability and Accountability Act (HIPAA), a federal law that protects patient health information.
Failing to meet regulatory compliance can be costly — in terms of both fines and reputational damage. In fact, 31% of respondents in the 2022 State of Kubernetes study reported customer or revenue loss due to a container compliance or security incident over the previous year.
Align your Teams to Ensure Cloud Security Compliance
For the success of any cloud deployment, you not only need the right skill set but also a clear understanding of roles and responsibilities. In other words, both IT leaders and developers need to be on the same page. Styra research suggests that’s not always the case when it comes to managing cloud security roles and responsibilities.
For example, 35% of IT decision-makers believe proving application compliance to external audits is considered a primary responsibility of IT infrastructure and operations teams, while only 21% of developers believe that IT infrastructure/operations teams should be responsible for these tasks.
When members of your team are out of sync, these gaps can lead to operational inefficiencies or security incidents. Different teams might be working on the same initiatives, leading to redundant work or neglected tasks because of uncertain responsibilities.
The takeaway: You need to align your IT operations and software development teams by defining roles and communicating responsibilities.
Start with These Container Compliance Frameworks
Some security and compliance frameworks offer guidance specifically for Kubernetes. Here are good starting points:
CIS Kubernetes Benchmark
The Center for Internet Security (CIS) offers a checklist of best practices to secure Kubernetes environments. Styra DAS offers a CIS Benchmarks Kubernetes compliance pack of rules mapped to corresponding CIS Benchmark requirements.
NIST SP 800-190 Container Security
The National Institute of Standards and Technology (NIST) has a series of guidelines targeting government agencies and contractors. The NIST SP 800-190 documentation focuses on increased container security posture.
Kubernetes PCI DSS Compliance
If your application handles electronic payments, it must adhere to the Payment Card Industry Data Security Standard (PCI DSS). Styra DAS offers a library with more than 70 controls specifically for Kubernetes PCI compliance.
Learn how Styra maps Kubernetes policies to PCI standards. Download our white paper.
MITRE ATT&CK Containers Matrix
The MITRE ATT&CK® framework outlines common tactics and techniques typically employed in cyberattacks. As part of its Enterprise Matrix, MITRE has a section dedicated to containerized workloads. Bootstrap compliance with the MITRE ATT&CK Containers Matrix with the Styra DAS MITRE ATT&CK Matrix for Kubernetes compliance pack.
Deploy Automated Container Compliance Tools
To simplify deployment and ease Kubernetes compliance burdens, you can use an automated tool such as Styra DAS.
Our solution is built on OPA and implemented directly via Kubernetes APIs. It is the fastest and easiest way to put guardrails around Kubernetes, providing the necessary compliance your organization needs.
Explore all the benefits of DAS for an enhanced Kubernetes security strategy. Download our product brief.
Get Detailed Kubernetes Audit Logs with Styra Compliance Packs
Our compliance-as-code approach enables you to use out-of-the box policies to map to specific compliance controls. We make it much easier with our Kubernetes compliance packs.
Styra offers coverage for:
- CIS Benchmarks
- PCI DSS v3.2
- MITRE ATT&CK®
- Kubernetes Best Practices
- Pod Security Policies
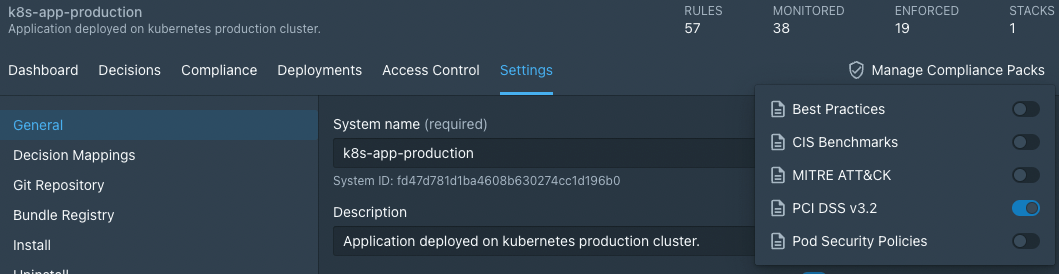
These are a group of policies mapped to standards, plus K8s audit logs that help you prove compliance. Through DAS, you can also run an analysis to ensure that your compliance measures won’t impact application performance. Your team can define guardrail controls and make compliance checks to identify violations at different stages, such as development, testing and deployment.
Take the Next Step Toward Improved Cloud Compliance
See in action how Styra DAS can help you automate K8s compliance monitoring and logging. Sign up now to try it for free.
Frequently Asked Questions
What is security compliance?
Compliance involves meeting best practices, guidelines or regulatory requirements, and being able to prove it, often through audits. Security compliance, in particular, refers to measures and access controls to ensure the protection of an organization’s assets, such as data, systems and devices.
What is compliance-as-code?
Compliance-as-code is the use of code to automate compliance controls, from establishing guardrails, verifying compliance and reporting. An example of compliance-as-code is the deployment of Styra DAS compliance packs, which offer a pre-built library of policies to help you meet compliance requirements and audit demands in K8s environments.
Check out the Styra DAS documentation page to learn how to add compliance packs into your Kubernetes system.
What is a Kubernetes admission controller?
A Kubernetes admission controller is a feature that monitors and manages what happens in a Kubernetes cluster. You can use Styra DAS as a Kubernetes admission controller because our solution provides a control plane to push policies to OPAs in the cluster and visualize their enforcement.
Download our white paper to learn more about Kubernetes security compliance through admission control.
Read More:
Authorization in Microservices
How to Secure Kubernetes Cluster