OPA Management
Manage the health and well-being of your OPAs, just like you would any other service.
Standardizing on Open Policy Agent
Production-ready OPA implementations require policy management, updates, distribution and monitoring as teams increase complexity by using different languages, tooling and logic.
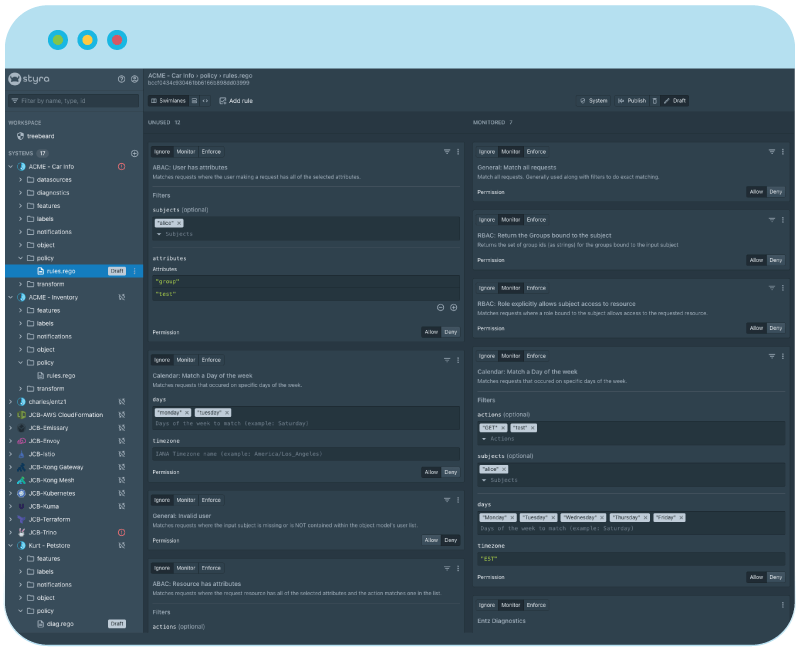
OPA Policy Management and Distribution
When policy is defined as code, it should be managed as code. With Git as the source of truth for describing deployments, all change requests must be handled as code and maintained in the Git repository.
Author policy through a UI, CLI or APIs and store subsequent policies in Git. Fetch policy bundles from Git and distribute them to the appropriate Open Policy Agent instances.
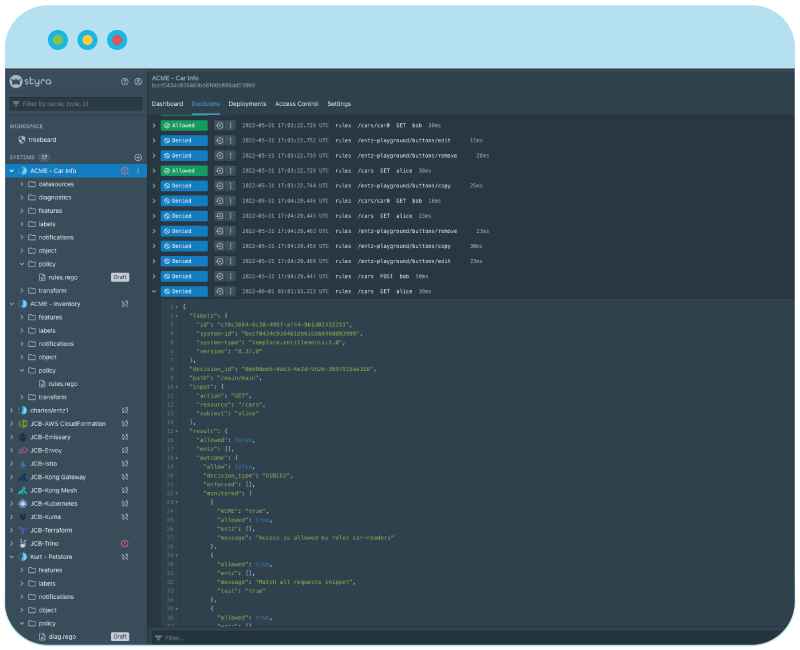
Real-time Data for Security & Compliance
Protect against intrusions, prevent lateral movement and hot patch policies globally to block attacks in real time. Decision logs can easily show the input and output of OPA decisions and notify security teams about outages or anomalous behavior through feeds to SIEMs and SecOps.
Distribute and manage security and compliance best practices across the business using policy as code.
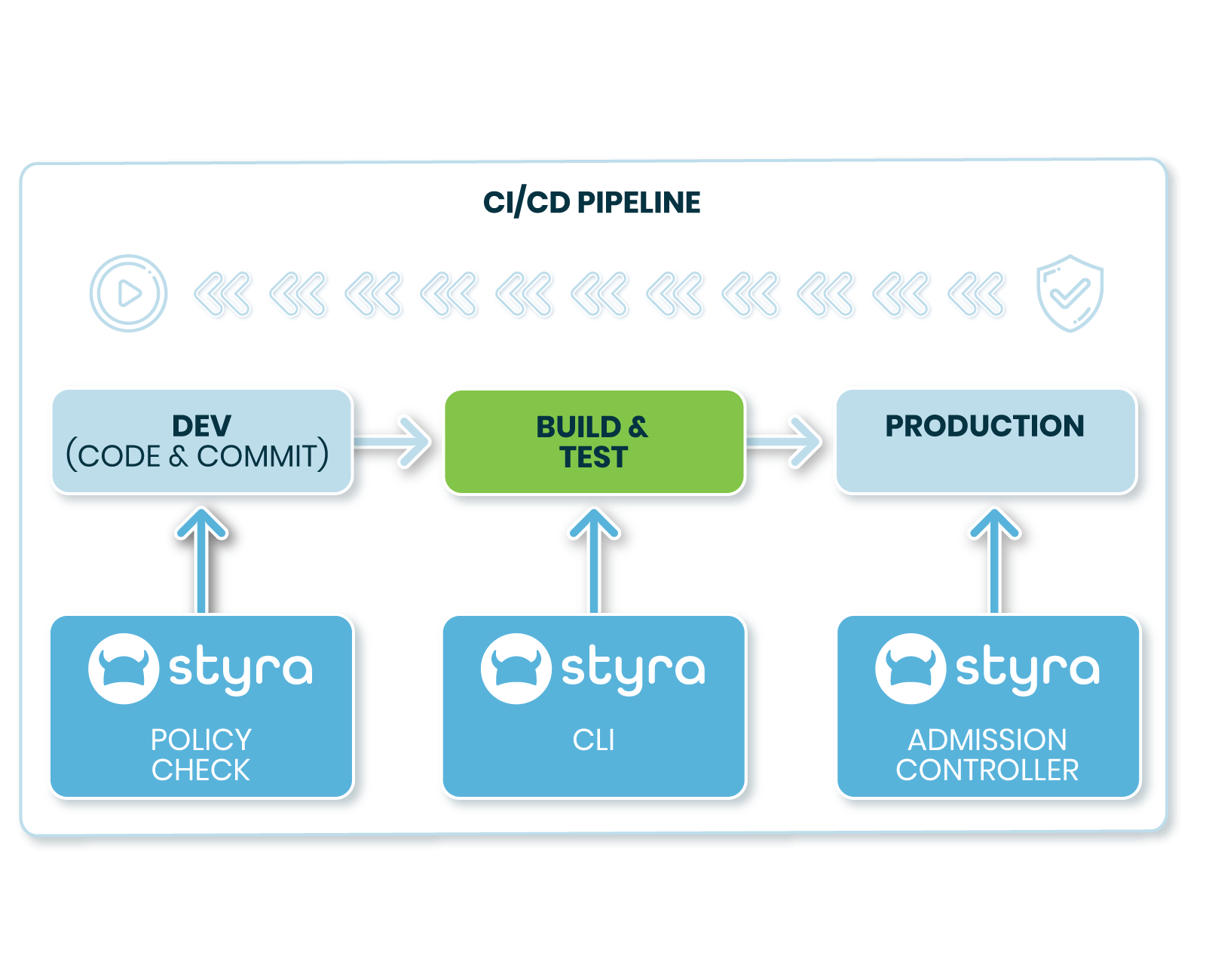
See Validation Before Runtime
Teams need a way to validate changes before committing them beyond GitOps peer reviews. Easily test new policy against a record of previous policy decisions, to evaluate the effect new policy changes will have, automatically.
Styra also offers a Decision Replay ability which ensures that policy changes end up with the expected results. Unit testing, compliance checking and policy output validation all mitigate the risk of human error and prevent downtime or accidental risk.
Improve Security with Shared Policy Libraries
Move beyond templates and macros to build, test and deploy policies that can be reused across teams at varying skill levels, as well as any clusters and clouds. Easily create and share a library of OPA policies and tests to improve deployment speed and reduce the risk of human error and dependency on Rego expertise.
When enterprises centralize policy as code and authorization with consistent best practices and standards, they can improve security and compliance. Learn more about Styra Policy Packs.
Build vs. Buy
We know you’ve thought about it – let us show you what it takes to get the outcomes your organization requires.
Cloud native
Authorization
Entitlement Explosion Repair
Join Styra and PACLabs on April 11 for a webinar exploring how organizations are using Policy as Code for smarter Access Control.
Speak with an Engineer
Request time with our team to talk about how you can modernize your access management.