Microservices Authorization
Low-latency, distributed authorization that scales with your microservices.
Fast, Distributed Authorization
Modern microservice architectures demand a modern authorization solution.
- Get fast, decentralized authorization everywhere your services run.
- Eliminate implicit trust between services.
- Scale elastically.
- Centralize authorization governance and keep team autonomy.
You can do all this with the Enterprise OPA Platform which combines fast, decentralized authorization and central governance. Give developers one standardized way to secure all your microservices using familiar workflows.
Authorization Platform Benefits for Microservices
Standardize Authorization
Standardize your authorization just like monitoring, logging, and deployment. Let developers build the future, not maintain siloed authorization.
Remove Latency
Get low-latency, distributed authorization to keep microservices both quick and secure. Let the flexible data fabric to equip every pod for instant authorization without the network latency. Elastically scale authorization with your workloads.
5X Faster to Zero Trust
Roll out Zero Trust authorization to your microservices 5X faster compared to homegrown solutions. Secure all the software you build using one flexible platform designed to work with your existing identities, data, and workflows.
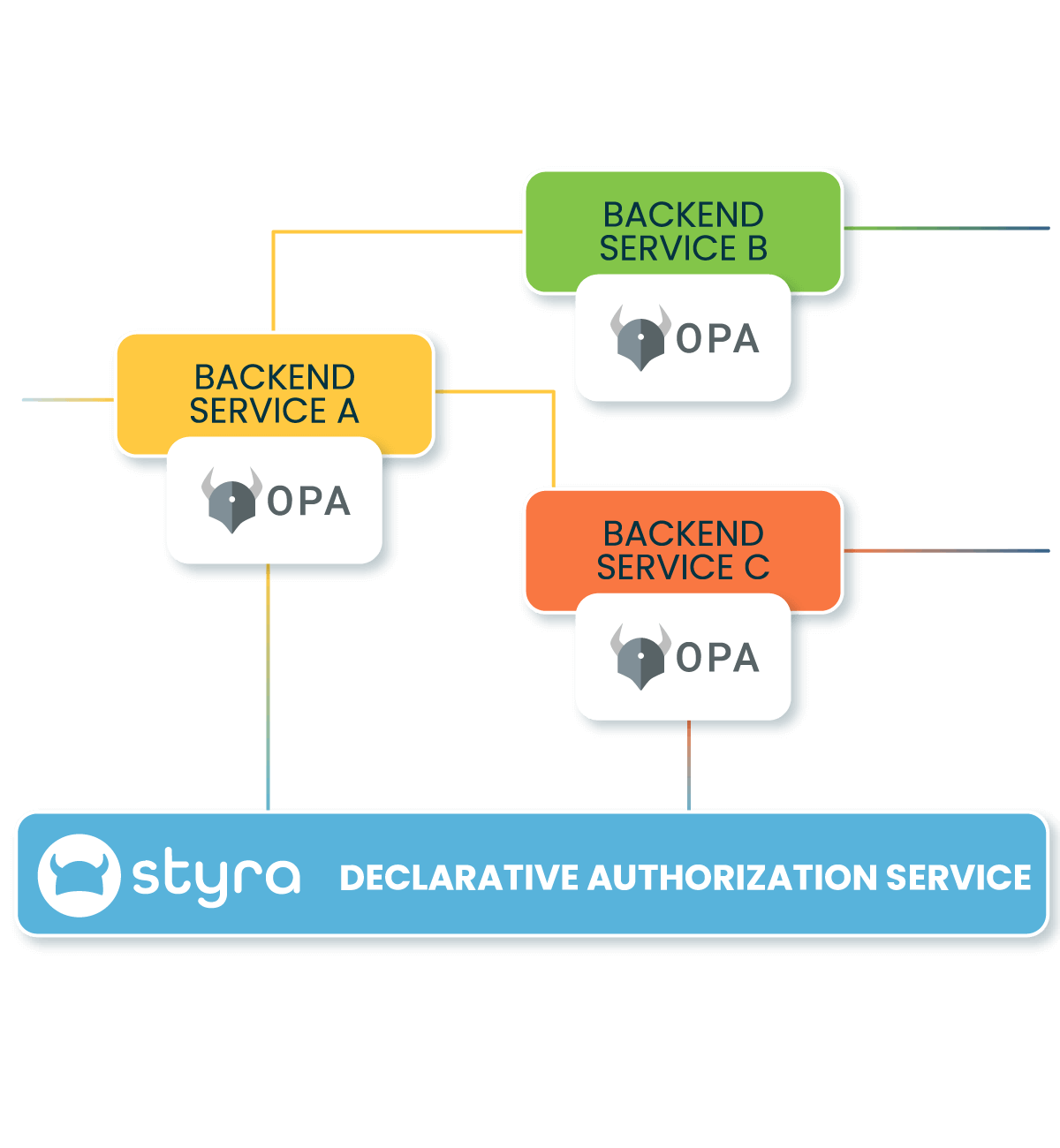
Eliminate Implicit Trust between Services
Enforce fine-grained authorization in service-to-service API calls based on non-human identities, workforce identities, and customer identities. Minimize lateral movement with a Zero Trust mindset. Use the platform that combines fast, decentralized enforcement with centralized management to secure your east-west traffic.
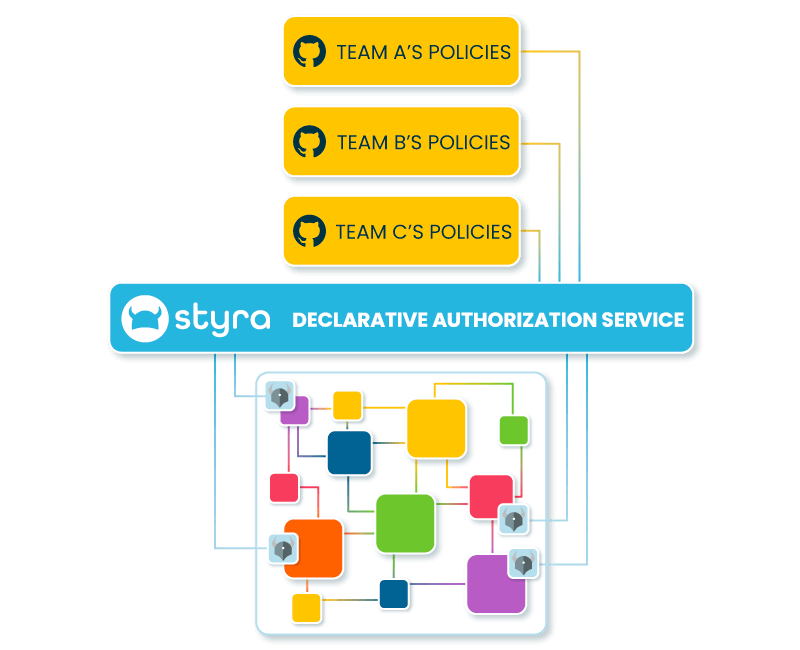
Central Governance and Team Autonomy
Enable high autonomy with high standards. Use global authorization policies and policy libraries to enable central governance, policy re-use, and faster time-to-market. Get the best of both worlds with this multi-tiered authorization management—central governance with team autonomy.
Rich Data Integrations
Make authorization decisions based on the full picture, informed by all your data sources. Skip the data access network latency and get fast decisions everywhere your services run.
Cloud native
Authorization
Entitlement Explosion Repair
Join Styra and PACLabs on April 11 for a webinar exploring how organizations are using Policy as Code for smarter Access Control.
Speak with an Engineer
Request time with our team to talk about how you can modernize your access management.